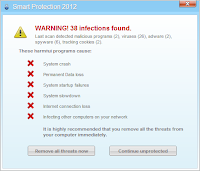
This was performed on a virtual machine
__________________________________________________________________________________
Looks very similar to
Security Antivirus. It definitely packs more of a punch though and I'm not just referring to the ZeroAccess rootkit that was bundled in the sample I ran.
Instead of modifying the hosts file, it creates hundreds (700+) of bad entries in this key: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\currentversion\
image file execution options.
This is something I needed to refamiliarize myself with as well. This article by a malware researcher at McAfee explained it very well (at least for me):
Image File Execution Options
For example, this line is from RogueKiller: [IFEO] HKLM\[...]\
Image File Execution Options :
taskmgr.exe (C:\Documents and Settings\infectedxp\Application Data\
Protector-cxf.exe task) -> DELETED

Task Manager was just one of the many applications that was hijacked and would launch the FakeAV if opened.
Just to reiterate, you are not
completely blocked from running Task Manager which is typically the case in the majority of FakeAVs. Most of the time the legitimate Task Manager will open and then immediately close and report that taskmgr.exe (Task Manager) is infected, remember? :-)
With this type of FakeAV, Task Manager does not give you any
errors, and
will launch,
but instead launches the FakeAV's version of Task Manager :grin
__________________________________________________________________________________
 |
| RogueKiller |
¤¤¤ Bad processes: 4 ¤¤¤
[SUSP PATH] Protector-cxf.exe -- C:\Documents and Settings\infectedxp\Application Data\
Protector-cxf.exe -> KILLED [TermProc]
[SUSP PATH] Protector-cxf.exe -- C:\Documents and Settings\infectedxp\Application Data\
Protector-cxf.exe -> KILLED [TermProc]
[RESIDUE] Protector-cxf.exe -- C:\Documents and Settings\infectedxp\Application Data\
Protector-cxf.exe -> KILLED [TermProc]
[RESIDUE] Protector-cxf.exe -- C:\Documents and Settings\infectedxp\Application Data\
Protector-cxf.exe -> KILLED [TermProc]
¤¤¤ Registry Entries:
756 ¤¤¤
[SUSP PATH] HKCU\[...]\Run : Inspector (C:\Documents and Settings\infectedxp\Application Data\
Protector-cxf.exe) -> DELETED
[IFEO] HKLM\[...]\Image File Execution Options : a.exe (svchost.exe) -> DELETED
[IFEO] HKLM\[...]\Image File Execution Options : aAvgApi.exe (svchost.exe) -> DELETED
[IFEO] HKLM\[...]\Image File Execution Options : AAWTray.exe (svchost.exe) -> DELETED
[IFEO] HKLM\[...]\Image File Execution Options : About.exe (svchost.exe) -> DELETED
[IFEO] HKLM\[...]\Image File Execution Options : ackwin32.exe (svchost.exe) -> DELETED
[IFEO] HKLM\[...]\Image File Execution Options : Ad-Aware.exe (svchost.exe) -> DELETED
[IFEO] HKLM\[...]\Image File Execution Options : adaware.exe (svchost.exe) -> DELETED
[IFEO] HKLM\[...]\Image File Execution Options : advxdwin.exe (svchost.exe) -> DELETED
¤¤¤ Infection : ZeroAccess ¤¤¤
[ZeroAccess] (LOCKED) windir\NtUpdateKBxxxx present!
I did not want to copy/paste all the information in this post due to its size. If interested, the full log can be obtained from here:
http://pastebin.com/Hq79yqJe
__________________________________________________________________________________
 |
| MBAM |
Registry Values Detected: 1
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System|
DisableRegedit (Hijack.Regedit) -> Data: 0 -> Quarantined and deleted successfully.
Files Detected: 1
C:\Documents and Settings\infectedxp\Application Data\
Protector-cxf.exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
__________________________________________________________________________________
 |
| TDSSKiller |
14:21:05.0039 0628 NetBT ( Virus.Win32.ZAccess.aml ) - infected
14:21:05.0039 0628 NetBT - detected Virus.Win32.ZAccess.aml (0)
14:21:16.0125 0632 C:\WINDOWS\system32\DRIVERS\netbt.sys - copied to quarantine
14:21:16.0255 0632 Backup copy found, using it..
14:21:16.0265 0632 C:\WINDOWS\system32\DRIVERS\netbt.sys - will be cured on reboot
14:21:16.0546 0632 NetBT ( Virus.Win32.ZAccess.aml ) - User select action: Cure
__________________________________________________________________________________
 |
| CF |
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
.
c:\windows\$NtUninstallKB35486$
c:\windows\$NtUninstallKB35486$\1629779852
c:\windows\$NtUninstallKB35486$\1842931526\@
c:\windows\$NtUninstallKB35486$\1842931526\cfg.ini
c:\windows\$NtUninstallKB35486$\1842931526\Desktop.ini
c:\windows\$NtUninstallKB35486$\1842931526\L\anjgdmvc
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List]
"11776:UDP"= 11776:UDP:UDP 11776
<--- Delete this value
"20573:UDP"= 20573:UDP:UDP 20573
<--- Delete this value
"21174:TCP"= 21174:TCP:TCP 21174
<--- Delete this value
"10118:TCP"= 10118:TCP:TCP 10118
<--- Delete this value
__________________________________________________________________________________
 |
| MGtools |
"C:\Documents and Settings\All Users\Start Menu\Programs\"
window~3.lnk Feb 23 2012 875 "
Windows Functionality Checker.lnk"
"C:\Documents and Settings\infectedxp\Desktop\"
window~1.lnk Feb 23 2012 841 "
Windows Functionality Checker.lnk"
"C:\Documents and Settings\infectedxp\Application Data\"
result.db Feb 23 2012 282 "
result.db"
__________________________________________________________________________________
Misc Notes:
Has a fancy loading screen :-P I did not screenshot this
MBAM "hanged" twice when trying to delete all the bad registry entries. Used RogueKiller instead.
No other residual OS damage. NetBT (internet related) was successfully restored with TDSSKiller.
___________________________________________________________________________________