________________________________________________________________________________
 |
| FRST |
HKLM\...\Run: [voitjxghtvngqbu] C:\Documents and Settings\All Users\Application Data\jhdmxqskgvmtxilxyiwh.exe [64512 2012-05-22] ()
HKU\thisisu\...\Run: [voitjxghtvngqbu] C:\Documents and Settings\All Users\Application Data\jhdmxqskgvmtxilxyiwh.exe [64512 2012-05-22] ()
HKLM\...\Winlogon: [Shell] explorer_new.exe [64512 2012-05-22] ()
2012-05-23 02:17 - 2008-04-14 11:00 - 0064512 ____A C:\Windows\explorer_new.exe
2012-05-23 02:16 - 2012-05-22 12:34 - 0000000 ____D C:\Documents and Settings\All Users\Application Data\lwxnrakwwvtxgsd
2012-05-23 02:15 - 2012-05-20 21:43 - 0000016 ____A C:\Documents and Settings\All Users\Application Data\seaoeidlvppzkholfzrrrrvkdflprazo
2012-05-23 02:15 - 2012-05-19 04:09 - 0064512 ____A C:\Documents and Settings\All Users\Application Data\jhdmxqskgvmtxilxyiwh.exe
2012-05-23 02:15 - 2012-05-17 21:50 - 0064512 ____A C:\Windows\jhdmxqskgvmtxilxyiwh.exe
MD5: 1303adf0a0aa3ff3b4a7c818c452853c - VT
Misc Notes:
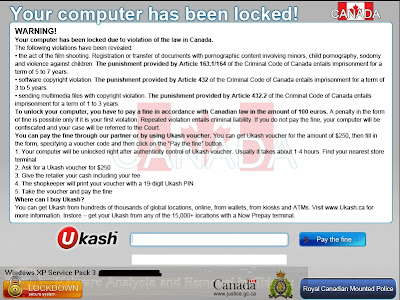
The folder in %allusersprofile%\appdata (C:\Documents and Settings\All Users\Application Data\lwxnrakwwvtxgsd) has about 10 pictures that compose the ransom screen.