This was performed on a live (not Virtual) machine.
 |
| RogueKiller |
¤¤¤ Registry Entries: 7 ¤¤¤
[SUSP PATH] HKLM\[...]\Run : VuCWtdJYrTTuTWk.exe (C:\Documents and Settings\All Users.WINDOWS\Application Data\VuCWtdJYrTTuTWk.exe) -> DELETED
[HJPOL] HKLM\[...]\System : DisableTaskMgr (1) -> DELETED
[HJ] HKCU\[...]\Internet Settings : WarnOnHTTPSToHTTPRedirect (0) -> REPLACED (1)
[WallPP] HKCU\[...]\Desktop : Wallpaper () -> REPLACED (C:\Documents and Settings\ali\Local Settings\Application Data\Microsoft\Wallpaper1.bmp)
[HJ] HKCU\[...]\Advanced : Start_ShowMyComputer (0) -> REPLACED (1)
[HJ] HKCU\[...]\Advanced : Start_ShowSearch (0) -> REPLACED (1)
[HJ] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> REPLACED (0)
¤¤¤ MBR Check: ¤¤¤
--- User ---
[MBR] 6c5ea126ce052b9f53b7c718ff0986f2
[BSP] 11d467b9f31927f29d49c85858b51038 : MBR Code unknown
Partition table:
0 - [XXXXXX] FAT16 [HIDDEN!] Offset (sectors): 63 | Size: 49 Mo
1 - [ACTIVE] NTFS [VISIBLE] Offset (sectors): 96390 | Size: 249933 Mo
User = LL1 ... OK!
User = LL2 ... OK!
__________________________________________________________________________________
 |
| SAS |
Rogue.VirusTrigger
HKCR\CLSID\{95E9BCC0-2E84-4500-8A9C-0B7A96769124}
HKCR\CLSID\{95E9BCC0-2E84-4500-8A9C-0B7A96769124}\InprocServer32
HKCR\CLSID\{95E9BCC0-2E84-4500-8A9C-0B7A96769124}\InprocServer32#ThreadingModel
HKCR\CLSID\{95E9BCC0-2E84-4500-8A9C-0B7A96769124}\ProgID
HKCR\CLSID\{95E9BCC0-2E84-4500-8A9C-0B7A96769124}\Programmable
HKCR\CLSID\{95E9BCC0-2E84-4500-8A9C-0B7A96769124}\TypeLib
HKCR\CLSID\{95E9BCC0-2E84-4500-8A9C-0B7A96769124}\VersionIndependentProgID
HKLM\Software\Classes\CLSID\{95E9BCC0-2E84-4500-8A9C-0B7A96769124}
HKCR\CLSID\{95E9BCC0-2E84-4500-8A9C-0B7A96769124}
HKCR\AnvTrgrWarning.WarningBHO.1
HKCR\AnvTrgrWarning.WarningBHO.1\CLSID
HKCR\AnvTrgrWarning.WarningBHO
HKCR\AnvTrgrWarning.WarningBHO\CLSID
HKCR\AnvTrgrWarning.WarningBHO\CurVer
HKCR\TypeLib\{BAE92F67-539C-41cd-9183-162BB40AAA0C}
HKCR\TypeLib\{BAE92F67-539C-41cd-9183-162BB40AAA0C}\1.0
HKCR\TypeLib\{BAE92F67-539C-41cd-9183-162BB40AAA0C}\1.0\0
HKCR\TypeLib\{BAE92F67-539C-41cd-9183-162BB40AAA0C}\1.0\0\win32
HKCR\TypeLib\{BAE92F67-539C-41cd-9183-162BB40AAA0C}\1.0\FLAGS
HKCR\TypeLib\{BAE92F67-539C-41cd-9183-162BB40AAA0C}\1.0\HELPDIR
HKU\S-1-5-21-1292428093-813497703-725345543-1003\Software\AnvTrgrsoft
C:\Program Files\WEBMEDIAVIEWER\myd.ico
C:\Program Files\WEBMEDIAVIEWER\mym.ico
C:\Program Files\WEBMEDIAVIEWER\myp.ico
C:\Program Files\WEBMEDIAVIEWER\myv.ico
C:\Program Files\WEBMEDIAVIEWER\ot.ico
C:\Program Files\WEBMEDIAVIEWER\ts.ico
C:\Program Files\WEBMEDIAVIEWER
HKU\S-1-5-21-1292428093-813497703-725345543-1003\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{95E9BCC0-2E84-4500-8A9C-0B7A96769124}
HKCR\Interface\{5C8B2A9C-24A0-4991-A74B-1E4931BD3A57}
HKCR\Interface\{5C8B2A9C-24A0-4991-A74B-1E4931BD3A57}\ProxyStubClsid
HKCR\Interface\{5C8B2A9C-24A0-4991-A74B-1E4931BD3A57}\ProxyStubClsid32
HKCR\Interface\{5C8B2A9C-24A0-4991-A74B-1E4931BD3A57}\TypeLib
HKCR\Interface\{5C8B2A9C-24A0-4991-A74B-1E4931BD3A57}\TypeLib#Version
Trojan.Media-Codec
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\System Alert Popup
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\System Alert Popup#DisplayName
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\System Alert Popup#UninstallString
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\System Alert Popup#InstDate
Rogue.WebMediaViewer
HKU\S-1-5-21-1292428093-813497703-725345543-1003\Software\WebMediaViewer
Trojan.Agent/Gen-RogueAntiSpy
C:\DOCUMENTS AND SETTINGS\ALL USERS.WINDOWS\APPLICATION DATA\CSJNAQKKDLC1G2.EXE
C:\DOCUMENTS AND SETTINGS\ALI\APPLICATION DATA\MICROSOFT\INTERNET EXPLORER\QUICK LAUNCH\SYSTEM FIX.LNK
C:\DOCUMENTS AND SETTINGS\ALI\DESKTOP\RK_QUARANTINE\VUCWTDJYRTTUTWK.EXE.VIR
C:\DOCUMENTS AND SETTINGS\ALI\DESKTOP\SYSTEM FIX.LNK
C:\DOCUMENTS AND SETTINGS\ALI\LOCAL SETTINGS\TEMP\592.TMP
C:\DOCUMENTS AND SETTINGS\ALI\LOCAL SETTINGS\TEMP\SMTMP\2\SYSTEM FIX.LNK
C:\DOCUMENTS AND SETTINGS\ALI\START MENU\PROGRAMS\SYSTEM FIX\SYSTEM FIX.LNK
C:\DOCUMENTS AND SETTINGS\ALI\START MENU\PROGRAMS\SYSTEM FIX\UNINSTALL SYSTEM FIX.LNK
C:\DOCUMENTS AND SETTINGS\ALL USERS.WINDOWS\APPLICATION DATA\VUCWTDJYRTTUTWK.EXE
C:\WINDOWS\Prefetch\CSJNAQKKDLC1G2.EXE-0E3467CF.pf
C:\WINDOWS\Prefetch\VUCWTDJYRTTUTWK.EXE-2737C7F1.pf
Browser Hijacker.Favorites
C:\DOCUMENTS AND SETTINGS\ALI\FAVORITES\ANTIVIRUS SCAN.URL
C:\RECYCLER\S-1-5-21-1292428093-813497703-725345543-1003\DC248.URL
C:\RECYCLER\S-1-5-21-1292428093-813497703-725345543-1003\DC249.URL
C:\RECYCLER\S-1-5-21-1292428093-813497703-725345543-1003\DC296.URL
C:\RECYCLER\S-1-5-21-1292428093-813497703-725345543-1003\DC297.URL
Trojan.Agent/Gen-Krpytik
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\AT102.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\HLLAPI32.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\HPVT.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\LK250.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\LK250DOS.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\LK450.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\MS_APPC.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\MS_LUA.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\RFC1006.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\SERIAL.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\SOCKSTUB.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\SSH.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\TELNET.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\TTACCESS.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\TTMREC.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\TTRUN.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\TTVER.DLL
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\WANG.DLL
Rootkit.ITGRDEngine
C:\PROGRAM FILES\TURBOSOFT\TTWIN3\BIN32\TTCOMP.DLL
__________________________________________________________________________________
 |
| MBAM |
Registry Keys Infected:
HKEY_CLASSES_ROOT\webmedia.chl (Trojan.Zlob) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\The Weather Channel (Adware.Hotbar) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Online Alert Manager (Trojan.Zlob) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Weather Services (Adware.Hotbar) -> Quarantined and deleted successfully.
Registry Values Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Control Panel\Cpls\wxfw.dll (Adware.Hotbar) -> Value: wxfw.dll -> Quarantined and deleted successfully.
Registry Data Items Infected:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_ShowControlPanel (PUM.Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_ShowHelp (PUM.Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_ShowMyDocs (PUM.Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_ShowRun (PUM.Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and deleted successfully.
Files Infected:
c:\documents and settings\ali\local settings\Temp\59E.tmp (Trojan.Dropper) -> Quarantined and deleted successfully.
c:\documents and settings\ali\my documents\My Music\My Music.url (Trojan.Zlob) -> Quarantined and deleted successfully.
c:\documents and settings\ali\my documents\my pictures\my pictures.url (Trojan.Zlob) -> Quarantined and deleted successfully.
c:\documents and settings\ali\my documents\my videos\My Video.url (Trojan.Zlob) -> Quarantined and deleted successfully.
__________________________________________________________________________________
 |
| CF |
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
.
c:\documents and settings\ali\Local Settings\Temporary Internet Files\viewChanges.html
c:\documents and settings\ali\Start Menu\Programs\System Fix
c:\documents and settings\ali\WINDOWS
c:\documents and settings\All Users.WINDOWS\Application Data\~CsJnaqKKDLC1G2
c:\documents and settings\All Users.WINDOWS\Application Data\~CsJnaqKKDLC1G2r
c:\documents and settings\All Users.WINDOWS\Application Data\CsJnaqKKDLC1G2
c:\documents and settings\All Users.WINDOWS\Application Data\TEMP
c:\documents and settings\Shamsa Ali\WINDOWS
c:\windows\EventSystem.log
c:\windows\Help\hp1100.hlp
c:\windows\system32\Cache
c:\windows\system32\SET1492.tmp
c:\windows\system32\SET1496.tmp
c:\windows\system32\SET149E.tmp
c:\windows\Update.bat
__________________________________________________________________________________
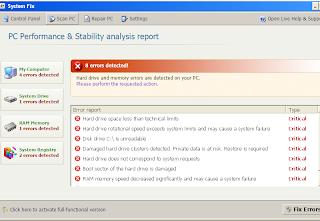
You are allowed to kill System Fix from Task Manager (RKill / RogueKiller not required)
Rootkit/hidden partition/MBR infection NOT included
The hidden partition you see is part of Dell Utilities
Places hidden attribute on entire OS drive.
__________________________________________________________________________________
Rootkit/hidden partition/MBR infection NOT included
The hidden partition you see is part of Dell Utilities
Places hidden attribute on entire OS drive.

No comments:
Post a Comment