This was performed on a live (not Virtual) machine.
Here is what was loaded when I first turned on the computer in Normal Mode.
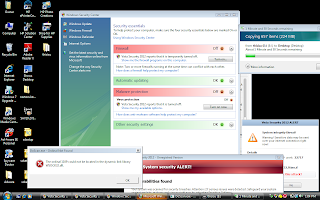
Lots of pop-ups as you see, this one was a bit more aggressive than some of the others I've seen.
On top of it all I would get constant application errors regarding Norton Antivirus. ZeroAccess rootkit had a snack ;-)
Here is the screen you will be brought to if you try to "activate" Vista Security 2012. Remember this is all faked and created by the malware creators.
__________________________________________________________________________________
 |
| RogueKiller |
¤¤¤ Bad processes: 2 ¤¤¤
[WINDOW : Vista Security 2012] ddj.exe -- C:\Users\Owner\AppData\Local\ddj.exe -> KILLED [TermProc]
[WINDOW : Vista Security 2012] ddj.exe -- C:\Users\Owner\AppData\Local\ddj.exe -> KILLED [TermProc]
¤¤¤ Registry Entries: 3 ¤¤¤
[HJ] HKLM\[...]\NewStartPanel : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> FOUND
[HJ] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> FOUND
[FILEASSO] HKLM\[...]Software\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command : ("C:\Users\Owner\AppData\Local\ddj.exe" -a "C:\Program Files\Internet Explorer\iexplore.exe") -> FOUND
¤¤¤ Particular Files / Folders: ¤¤¤
¤¤¤ Driver: [LOADED] ¤¤¤
¤¤¤ Infection : Rogue.AntiSpy-AH ¤¤¤
¤¤¤ HOSTS File: ¤¤¤
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: +++++
--- User ---
[MBR] 47e38b333fde87e38dd55d5145eda893
[BSP] 2322b9887f89ec6bfba12db29d773349 : Windows Vista MBR Code
Partition table:
0 - [ACTIVE] NTFS [VISIBLE] Offset (sectors): 2048 | Size: 160038 Mo
User = LL1 ... OK!
User = LL2 ... OK!
+++++ PhysicalDrive1: +++++
--- User ---
[MBR] 8da38b9ec667eb12484664792003e81b
[BSP] 9c39957118038b3040b5edd3b3224b1e : Windows 7 MBR Code
Partition table:
0 - [ACTIVE] NTFS [VISIBLE] Offset (sectors): 2048 | Size: 8034 Mo
User = LL1 ... OK!
Error reading LL2 MBR!
[WINDOW : Vista Security 2012] ddj.exe -- C:\Users\Owner\AppData\Local\ddj.exe -> KILLED [TermProc]
[WINDOW : Vista Security 2012] ddj.exe -- C:\Users\Owner\AppData\Local\ddj.exe -> KILLED [TermProc]
¤¤¤ Registry Entries: 3 ¤¤¤
[HJ] HKLM\[...]\NewStartPanel : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> FOUND
[HJ] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> FOUND
[FILEASSO] HKLM\[...]Software\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command : ("C:\Users\Owner\AppData\Local\ddj.exe" -a "C:\Program Files\Internet Explorer\iexplore.exe") -> FOUND
¤¤¤ Particular Files / Folders: ¤¤¤
¤¤¤ Driver: [LOADED] ¤¤¤
¤¤¤ Infection : Rogue.AntiSpy-AH ¤¤¤
¤¤¤ HOSTS File: ¤¤¤
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: +++++
--- User ---
[MBR] 47e38b333fde87e38dd55d5145eda893
[BSP] 2322b9887f89ec6bfba12db29d773349 : Windows Vista MBR Code
Partition table:
0 - [ACTIVE] NTFS [VISIBLE] Offset (sectors): 2048 | Size: 160038 Mo
User = LL1 ... OK!
User = LL2 ... OK!
+++++ PhysicalDrive1: +++++
--- User ---
[MBR] 8da38b9ec667eb12484664792003e81b
[BSP] 9c39957118038b3040b5edd3b3224b1e : Windows 7 MBR Code
Partition table:
0 - [ACTIVE] NTFS [VISIBLE] Offset (sectors): 2048 | Size: 8034 Mo
User = LL1 ... OK!
Error reading LL2 MBR!
__________________________________________________________________________________
C:\Windows\system32\drivers\afd.sys - will be cured on reboot
AFD ( Rootkit.Win32.ZAccess.aml ) - User select action: Cure
__________________________________________________________________________________
 |
| CF |
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
.
c:\windows\$NtUninstallKB40500$
c:\windows\$NtUninstallKB40500$\2367755029\@
c:\windows\$NtUninstallKB40500$\2367755029\bckfg.tmp
c:\windows\$NtUninstallKB40500$\2367755029\cfg.ini
c:\windows\$NtUninstallKB40500$\2367755029\Desktop.ini
c:\windows\$NtUninstallKB40500$\2367755029\keywords
c:\windows\$NtUninstallKB40500$\2367755029\kwrd.dll
c:\windows\$NtUninstallKB40500$\2367755029\L\qnbwvoto
c:\windows\$NtUninstallKB40500$\2367755029\lsflt7.ver
c:\windows\$NtUninstallKB40500$\2367755029\U\00000001.@
c:\windows\$NtUninstallKB40500$\2367755029\U\00000002.@
c:\windows\$NtUninstallKB40500$\2367755029\U\00000004.@
c:\windows\$NtUninstallKB40500$\2367755029\U\80000000.@
c:\windows\$NtUninstallKB40500$\2367755029\U\80000004.@
c:\windows\$NtUninstallKB40500$\2367755029\U\80000032.@
c:\windows\$NtUninstallKB40500$\753632677
.
.
c:\windows\$NtUninstallKB40500$
c:\windows\$NtUninstallKB40500$\2367755029\@
c:\windows\$NtUninstallKB40500$\2367755029\bckfg.tmp
c:\windows\$NtUninstallKB40500$\2367755029\cfg.ini
c:\windows\$NtUninstallKB40500$\2367755029\Desktop.ini
c:\windows\$NtUninstallKB40500$\2367755029\keywords
c:\windows\$NtUninstallKB40500$\2367755029\kwrd.dll
c:\windows\$NtUninstallKB40500$\2367755029\L\qnbwvoto
c:\windows\$NtUninstallKB40500$\2367755029\lsflt7.ver
c:\windows\$NtUninstallKB40500$\2367755029\U\00000001.@
c:\windows\$NtUninstallKB40500$\2367755029\U\00000002.@
c:\windows\$NtUninstallKB40500$\2367755029\U\00000004.@
c:\windows\$NtUninstallKB40500$\2367755029\U\80000000.@
c:\windows\$NtUninstallKB40500$\2367755029\U\80000004.@
c:\windows\$NtUninstallKB40500$\2367755029\U\80000032.@
c:\windows\$NtUninstallKB40500$\753632677
__________________________________________________________________________________
 | |
| MGtools |
"C:\Users\Owner\AppData\Local\"
kb316p~1 Jan 10 2012 9208 "kb316pt716feqc24537sy13050q20yb545k0qc1w1dk647"
"C:\Users\Owner\AppData\Roaming\Microsoft\Windows\Templates\"
kb316p~1 Jan 10 2012 9208 "kb316pt716feqc24537sy13050q20yb545k0qc1w1dk647"
kb316p~1 Jan 10 2012 9208 "kb316pt716feqc24537sy13050q20yb545k0qc1w1dk647"
"C:\ProgramData\"
kb316p~1 Jan 10 2012 9208 "kb316pt716feqc24537sy13050q20yb545k0qc1w1dk647"
__________________________________________________________________________________
Misc notes:
Residual OS Damage: Windows Firewall broken - Repaired after all traces of malware were gone.I did scan with SAS first (found 6 threats) but I forgot to save the log for review :(
MBAM found 0 threats after SAS was run.
___________________________________________________________________________________




No comments:
Post a Comment