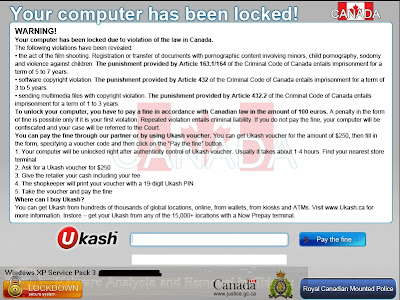
 |
Figure 1.a |
This is very similar to Gendarmerie Nationale (French) in the sense that the bad files are practically located in the same directories.
For this one, look in these directories:
- %userprofile%\local settings\temp\<random 10 letter folder> - For example: Mlqjqjqjq
- %windir%\system32
Note: The .exe in each folder listed is exactly the same in terms of MD5 hash, but the actual Name of the randomized .exe is different (both are randomized).
First step is remove the Windows lockout portion of this infection.
Boot off a diagnostic CD/DVD such as Hiren, or slave the hard drive to another PC with a bootable Windows OS.
Having seen this type of infection before, I just went into the suspected folders above and deleted the two bad .exe files from there. Once this is done, you should be able to boot to the Windows desktop again. If you'd like to use some type of scanning tool and know how to analyze the log, I'd recommend Farbar Recovery Scan Tool (FRST).
 |
| Back in Windows |
Great, we are back to the Windows desktop! Wait... why are all my files encrypted?!
Similar to ACCDFISA, this type of ransom trojan has two main features.
1) Lock you out of Windows (See Figure 1.a above)
2) Encrypts the majority of your files
Do not fret, the expert personnel at Kaspersky have created a tool called RannohDecryptor designed to decrypt and restore your files with ease!
 |
| Kaspersky RannohDecryptor in action |
 |
| After decryption |

useful :)
ReplyDeleteLifesaver - thank you :)
ReplyDeleteThank you both :)
ReplyDelete